
Information-theoretic security is a standard of cryptography that cannot be broken, even with unlimited computational power and time. The foundation of information-theoretic security is the use of an encryption process to introduce enough randomness and uncertainty that the output (ciphertext) appears completely random to anyone who does not possess the decryption key. The ciphertext does not reveal any patterns or provide any information that could lead to deducing the plaintext or the encryption key. This makes the encryption secure against all conceivable forms of attack.
Information-theoretic security is the highest level of security because it guarantees permanent security because it’s unaffected by advances in mathematics or computing power. Achieving this level of security in practice is very challenging. Here we discuss two possible paths to information-theoretic security: a classical approach using a One Time Pad (OTP) and a quantum approach using Quantum Secure Communications (QSC).
The One Time Pad (OTP)
When applied correctly, the One Time Pad (OTP) is widely recognized as the only classical encryption method that is perfectly secure. This method requires that each encryption key be used exactly once and never reused. OTP is secure against quantum attacks in principle when implemented with a statistically unbiased key, meaning that the encrypted message gives away nothing about the encryption key. OTP does this by mixing the original message (plaintext) with a secret key to create an unreadable output, called ciphertext. One of the simplest and most secure ways to do this is by using an operation called XOR, which flips bits in the message based on the key. If the key is truly random and used only once, the result is perfectly secure.
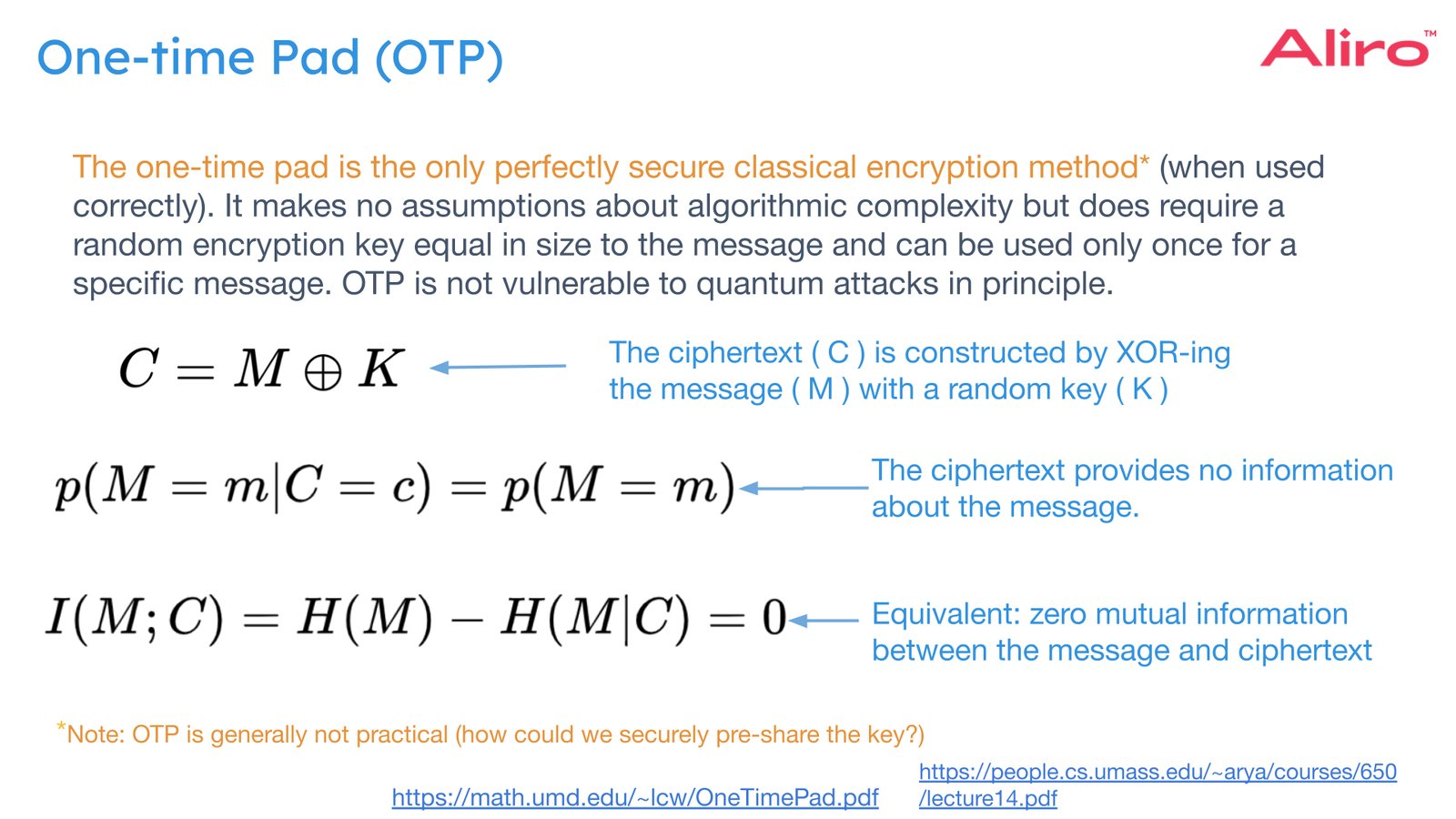
In most cases, OTP is extremely difficult to use in practice. The main challenge is key management: each message requires a unique key that is as long as the message itself. The key must also be shared between sender and receiver in a perfectly secure manner. If such a secure channel existed, then generating a key would not be necessary, as the secure channel itself could be used to send the secret message. Another practical challenge to using OTP is in the case of continuous secure communication: a new key of a length equivalent to the data must be continuously generated and shared in real time. For example, if Alice sends a 100-character message, she and Bob must share a 100-character random key, used only one time. This makes OTP cumbersome for transmitting massive amounts of data, or data that requires continuous secure connections. Despite offering information-theoretic security, the strict key requirements and distribution challenges limit the use of OTP to highly controlled, specialized environments.
Quantum Secure Communication Protocols
Communication protocols such as teleportation and quantum secure direct communication (QSDC) are quantum methods of achieving information-theoretic security. These protocols leverage unique quantum properties, highlighted below, to enhance security and communication capabilities across networks. The primary objective of these protocols is to distribute entanglement between nodes.
Entanglement. Entanglement is a phenomenon where two particles, such as a pair of photons, become related in such a way that their states are connected, regardless of the distance separating them. If one of these particles is measured, then the state of the other particle is also instantly known. In quantum secure networking, entanglement is a valuable resource because any attempt to eavesdrop on the quantum channel is almost immediately detectable.

In the example above, the first blue box shows two independent quantum systems, A and B. Their combined state can be written as a product of the two systems (a tensor product). Measuring particle A tells you nothing about particle B.
The equation in the second blue box describes an entangled system. In this case, the states of particles A and B can no longer be separated into two independent parts. Once entangled, these systems cannot be described by a tensor product. Instead, they exist in a state of superposition. In this state, any measurement of A instantly determines the state of B.
No-cloning Theorem. This theorem states that it is impossible to create an exact copy of an unknown quantum state. In other words, quantum information can’t be duplicated without changing it in ways that are easily detectable. This underpins the security of quantum communications.
State distinguishability. State distinguishability refers to the limits of what can be known about a quantum state without prior knowledge of how it was prepared. The ability to tell quantum states apart depends on their orthogonality, or how different they are from each other. Non-orthogonal states overlap in some way, making them impossible to differentiate between with certainty. Because of this, protocols that encode information in non-orthogonal states, any attempt at eavesdropping will disturb the quantum state and alert the legitimate parties that interception has occurred.
It’s clear that the landscape of secure communication is changing. While classical cryptography will remain essential, new protocols enabled by Quantum Networks are redefining the level of security that’s possible. Quantum Networking promises stronger, tamper-evident protection, as well as new capabilities. Preparing your cybersecurity infrastructure for Quantum Secure Communications means taking proactive steps today: adopting crypto-agile practices so new encryption methods can be implemented swiftly, testing quantum-safe solutions, and planning for the integration of quantum technologies into your existing network frameworks. These efforts combined lay the foundation for secure, resilient, and future-ready networks.
