
In this article Aliro Solutions Engineer Daniel Winton explains security vulnerabilities posed by quantum technology, plus the methods for mitigating those risks.
This article is an abbreviated excerpt from a webinar with Aliro Solutions Engineer Daniel Winton that first aired on Bright Talk. You can view the full webinar here.
Quantum Technology: what is it and how does it work?
Quantum physics is the branch of physics that describes the behavior of very small objects, on the scale of atoms and subatomic particles. Things operate very differently on the quantum scale than they do at the scale that we interact with normally in our day-to-day life. There are some useful and amazing properties that arise in quantum physics that quantum technology takes advantage of. I’m only going to briefly share three of those properties here.
To understand how quantum technology leverages quantum physics, we first need to understand the quantum bit. Quantum bits, or qubits, are the quantum version of classical bits. Just as classical bits are the basic unit of information that classical devices like your phone and your computer are built on, quantum bits are the basic unit of quantum information that quantum computers, quantum networks, and the Quantum Internet are and will be built on. While classical bits and quantum bits are analogous in this way, they behave very differently.
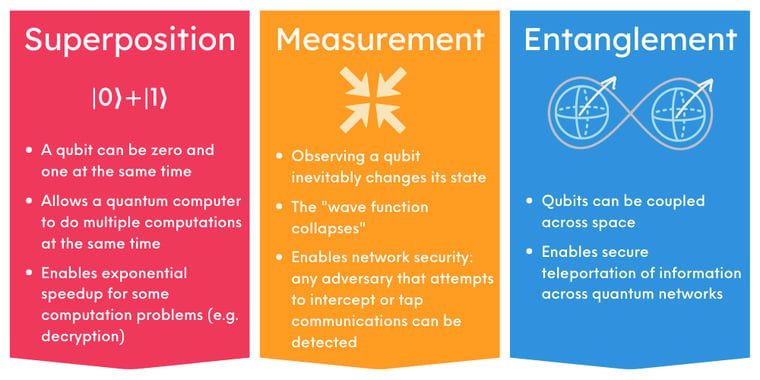
Superposition
Quantum bits have many quantum properties that classical bits do not. The classical bit stores one value of information: it either has value zero, or value one. Qubits can be a zero, a one, or some combination of these two values. When a quantum bit is a combination of zero and one, we say it's in a superposition of these two values. Because qubits can simultaneously be a zero and one, quantum computers are then able to do multiple computations at once. This enables computing speed-up for many difficult problems.
Measurement
Measuring or observing a qubit “collapses” it into a single value. For example: You might send me a qubit in a superposition of zero and one, meaning it could be zero or one, or some value in between. When I receive the qubit, I measure it: I test whether the qubit is a zero or one. The qubit is going to be exactly zero or exactly one once I measure it, and it can no longer be in a combination of these two values. Because measurement collapses a qubit's superposition, it is critical for quantum security: it can be used to detect an eavesdropper who intercepts a quantum message. For example, if you sent me an encryption key using qubits and that message is intercepted, the interception will change the value of that quantum message, alerting us to the fact that the key is no longer secure.
Entanglement
Qubits can be coupled together in such a way that measuring one qubit will affect the state of the other qubit, or even multiple other qubits. This type of coupling is known as entanglement. Qubits coupled in this way are entangled. The amazing thing about entanglement is that measuring one qubit will immediately affect the state of the qubit or the qubits it is entangled to, even if these qubits are many light years apart. This is the "spooky action at a distance" that upset Einstein (and many other physicists) in the early early 20th century. Entanglement is a foundational property that quantum technologies are built on. For example, without entanglement, quantum computers couldn’t be faster than classical computers. Entanglement is vital for the exciting applications that quantum technology will enable - like efficient drug discovery, cleaner materials science, and breakthroughs in imaging.
Quantum technology promises a wide range of fantastic benefits; it also poses potentially catastrophic, urgent security threats.
Quantum computers are a big threat to our cybersecurity. Shor's algorithm, perhaps the most famous quantum algorithm, can be used by quantum computers to do certain math problems, such as factoring large numbers and computing discrete logarithms, exponentially faster than what’s possible with classical technology. Quantum computers capable of running Shor's algorithm will be able to break the asymmetric key schemes such as RSA, DSA, and Diffie-Hellman, that we rely upon for authentication and key distribution. Authentication and key distribution are absolutely vital to cybersecurity. Essentially, all information that is sent across the Internet will be rendered insecure by future quantum computers. This is going to impact everyone: governments, businesses, and individuals. Defensive and military data, intellectual property, financial and medical records, and even infrastructure operations like electricity and water management all rely on key schemes that are at risk. It's easy to imagine just how disastrous it could be if this information falls into the wrong hands.
Shor's algorithm has existed for almost 30 years, and it's been proven to efficiently crack these vital security schemes. It's just a matter of time before quantum computing technology is advanced enough to run Shor's algorithm on large inputs. Experts predict that such quantum computers will exist by the end of the decade. The day in which quantum computers can break these current in-use security schemes is often referred to as “Q Day." Q Day may not happen until the end of the decade, but that doesn’t mean we have until the end of the decade to worry about quantum attacks. The information we are sending today is also at risk due to Harvest Now Decrypt Later attacks. Harvest Now Decrypt Later (HDNL) attacks are attacks in which an adversary steals encrypted data that they can't currently decrypt. The adversary holds onto this encrypted data until they're able to decrypt it. In the case of Q Day, that would be when they have access to a quantum computer capable of running Shor's algorithm. A lot of the information we send today, and that we're going to be sending in the foreseeable future, needs to remain secure for long periods of time and well past 2030. Because of the looming threat of Q Day, and the immediate threat of Harvest Now Decrypt Later, we need to come up with a countermeasure to this quantum threat as soon as possible.
Methods being deployed today to mitigate security risks from quantum threats
Post Quantum Cryptography (PQC)
PQC replaces the currently in-use classical security algorithms that will be broken by quantum computers, with classical security algorithms that are designed to be quantum safe. These new security algorithms are based on math problems that are believed to be difficult for quantum computers to solve. PQC is a purely classical solution, and it can be deployed over the classical internet. That means it’s comparatively quick and easy to implement, and for this reason is thought of as a good short-term solution. However, PQC algorithms are not mathematically proven to be secure. PQC algorithms could be broken in the future by quantum or even classical computers. This isn't just a theoretical issue with PQC. Two of the most promising PQC algorithms, RAINBOW and SIKE, were broken by regular classical computers – not even supercomputers were required to crack them. RAINBOW was cracked in less than a weekend and SIKE was cracked basically in a single hour. Lack of provable security makes PQC a risky long-term solution.
Quantum Key Distribution (QKD)
Quantum Key Distribution, QKD, typically refers to prepare-and-measure quantum key distribution protocols that run on and are enabled by prepare-and-measure networks known as QKD networks. This is a physics-based solution, relying on the properties of superposition and measurement. You can use these quantum properties to always detect the presence of an eavesdropper. Because of this, you can use quantum information to establish a key that you're sure has not been intercepted. In theory, or at the protocol level, this works great. However, there are implementation vulnerabilities such as with using trusted relay nodes which makes this less secure in practice. To use QKD to distribute a key between too far apart nodes, you'll need to use trusted relay nodes. The “trusted” part of this term is misleading. Trusted relay nodes are not nodes you can trust, but nodes that you must trust. If they become compromised, your key will become compromised as well. QKD networks also require the deployment of additional resources, such as QKD devices, and potentially additional optical fiber. QKD networks only support the single purpose of key distribution. An ideal solution would not have implementation vulnerabilities, and would have multi-purpose applications that enable more than just key distribution.
Quantum Secure Communication (QSC)
Quantum Secure Communications, QSC, is used to refer to the entanglement-based security protocols that run over and are enabled by entanglement-based quantum networks. This is a physics-based solution, relying on the property of entanglement. Similarly to QKD protocols, you can use these quantum properties to always detect the presence of an eavesdropper. You can use this quantum information to establish a key that you're sure has not been intercepted. Not only does this work great in theory, or at the protocol level, it also works great at the implementation level. The use of entanglement in QSC allows us to overcome many of the implementation issues that plague QKD. In QSC, entanglement-based quantum teleportation is used to send quantum information to endpoints on the network, and the quantum information is never exposed on the network itself. QSC runs over entanglement-based quantum networks, which are multi-purpose networks. The QSC security schemes have been around for decades, just waiting for the technology to develop to the level they can actually be used. These schemes have been tested and verified. The technology is developing fast, entanglement-based quantum networks are popping up all around North America and the world. Some of these networks have actually been able to test and run QSC.
Hybrid methodology
One popular proposed solution is to use PQC and QSC together. PQC is a good short-term solution, and we're going to need the provable security and value of QSC long-term. Using a hybrid PQC / QSC solution together will be at least as strong as each solution on its own. A hybrid solution can only be compromised if both the PQC and QSC algorithms involved are compromisedMitigating security vulnerabilities and leveraging the benefits of quantum technology
Quantum Secure Communication (QSC) enabled by entanglement-based quantum networks, is an important and effective countermeasure to the looming quantum threat. The implementation of QSC is secure in part because of quantum teleportation, which allows us to communicate quantum information between users of a network without that quantum information ever being exposed on the network. This means that even if a midpoint of the network is compromised, the quantum data will not be compromised.
QSC is an excellent value. With Quantum Secure Communication, the same entanglement-based quantum networks that enable this solution will enable advancements in computing, sensing, and future distributed quantum applications. QSC is implementable near term. The security schemes exist and have been verified; entanglement-based quantum networks that are capable of running these schemes exist and are being built today.
