
There are key technologies required to allow an entanglement-based secure network to scale to more nodes and across larger distances. The technology that is needed for implementing an entanglement-based secure network must be able to generate, manipulate, transmit, store, and measure quantum information. To make full-scale, wide-area quantum network deployments practical, the quantum and classical hardware and software technologies must be scalable, maintainable, sufficiently cost-effective, and efficient.
Free space optics
Free space optics will play a key role in extending the quantum network across very long distances. For example, using satellites and/or laser telescopes to communicate to a series of ground stations, which are geographically very far apart. Relative to optical fiber, free space channels can transmit quantum information over much longer distances because quantum signals experience much less attenuation and scattering losses in a free space link. Additionally, free space channels can be easily redirected to reach different geographic locations and mobile nodes. These factors make free space optics a much more attractive technology than, say, a chain of many quantum repeaters on a terrestrial fiber channel to make very distant connections.
Photon sources and detectors
As expected, the higher the quality of the network’s components, the greater distances and higher performance the network can achieve. Having high-efficiency photon sources and photon detectors will ensure that a sufficient number photons travel across the channel and arrive where needed, and then also detected on arrival with more efficiency. Higher-quality quantum networking hardware also enables longer distances. This holds true for quantum memories (e.g. long storage time and retrieval efficiency), and also light-matter interfaces (e.g. for efficient transduction to/from the optical domain).
Optimized protocols
From the software perspective, optimized and efficient quantum and classical communication protocols enable higher entanglement generation rates, higher end-to-end entanglement fidelity, and longer distances between nodes. These protocols govern the behavior of the nodes. For example, such protocols will govern how resources in the network are managed, how and when nodes transmit and encode information, how and when they receive and decode information, and what actions to take depending on network events. Tuning protocols and using the resources of the network in an optimal manner will also make for higher and more equitable rates and fidelities across distances, users, and applications. Coordinating this complex “dance” in a large-scale quantum network requires an innovative, sophisticated, and tightly-synchronized software and protocol stack.
Quantum repeaters
Quantum repeaters are a key technology in enabling entanglement-based quantum networks at-scale. The primary function of a quantum repeater in the near term is to conduct an operation called entanglement swapping, which essentially extends the physical distance of the entanglement. 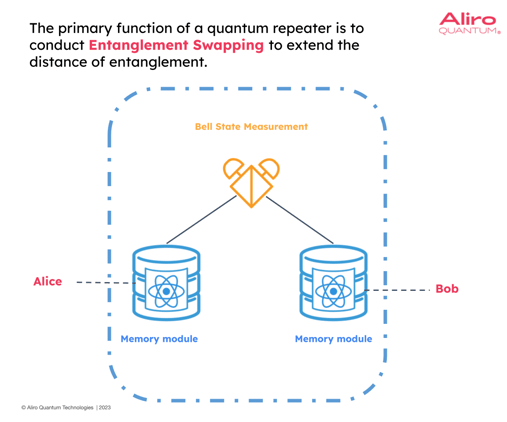
In the example above, there is an entanglement between Alice and a memory module in a repeater. And similarly, Bob is entangled with another memory module at a repeater. Once these entanglements have been established, the stored photons can be sent to a Bell state measurement station to perform the entanglement swapping operation. This extends the distance of the entanglement such that now Alice and Bob are directly entangled.
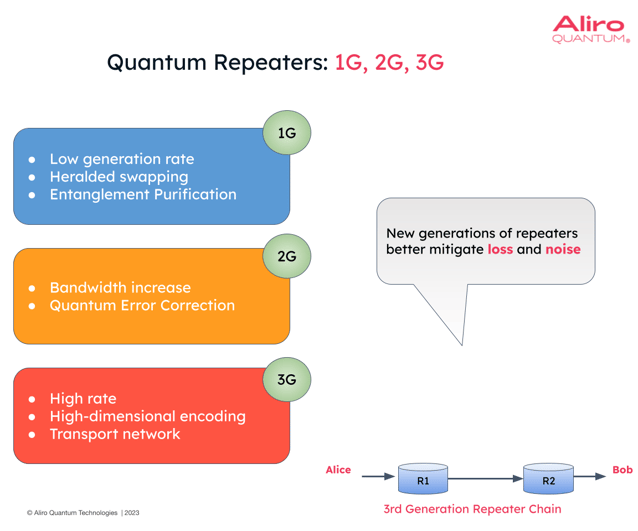
Quantum repeaters are actively being commercially developed and will undergo an evolution over time, improving upon previous generations’ performance. Each new generation will become better at mitigating the two biggest hurdles in entanglement-based networking: loss and noise.
-
- First generation quantum repeaters:
These are the repeaters outlined in the example above. They can conduct entanglement swapping operations in a heralded manner and it will be known if the swapping operation was successful or not. They may also have the ability to do some entanglement purification as well: purification (or sometimes called distillation) is a way to boost the fidelity of your usable entanglement, even as it’s being distributed via the repeaters.
- First generation quantum repeaters:
-
- Second generation quantum repeaters:
These quantum repeaters will show a tangible bandwidth increase, meaning they are better at the task of distributing entanglement at a higher rate and higher fidelity. In this generation, quantum error correcting codes are introduced. These repeaters will mature to have some quantum processing capabilities, i.e. to perform operations on these quantum states at the repeater. They will be able to run error-correcting codes to detect and correct for errors that may have occurred on the quantum state.
- Second generation quantum repeaters:
-
- Third generation quantum repeaters:
This generation is a paradigm shift. In the first and second generations, there are only short distance entanglements, and the entanglements are sort of “glued” together via entanglement swapping, extending the distance of the entanglement. Third generation repeaters (sometimes called one-way repeaters) behave like a transport network, more akin to the classical networks of today. These repeaters are designed and built to physically transport data from point A to point B through a kind of feed-forward relay network. These operate at high rates, and instead of using single photons, it’s now possible to encode the quantum state in a higher-dimensional space using numerous photons, thus enabling the transport network paradigm.
- Third generation quantum repeaters:
Quantum routers
Quantum routers are really just quantum repeaters with more input/output interfaces to the network, enabling more complex topologies and potentially multipartite entanglement: instead of entangling just Alice and Bob, now there is the ability to entangle Alice, Bob and Charlie. Quantum routers will play a key role in the evolution of entanglement-based quantum networks.
Multiplexing
As entanglement-based quantum networks scale up, longer distance links will be required. Multiplexing will help networks take advantage of these longer distances and to maintain as high a generation rate and fidelity as possible. Multiplexing has been done in classical networking, and entanglement-based quantum network will have a quantum equivalent. In an entanglement-based quantum network, there are many different signals traversing the network: quantum states encoded in single photons or potentially in a higher-dimensional state with numerous photons, and classical traffic traversing the network for communicating messages, clock signals, and measurement data. All of these signals need to coexist on the network and be traversing simultaneously; multiplexing technology provides a number of ways to efficiently encode and decode these signals over a single channel or set of channels such that errors are minimized and bandwidth/quality are maximized. There are a variety of ways to do this, e.g. with wavelength-division, time-division, or spatial multiplexing of the signals.
Using a full-scale entanglement-based quantum network to its fullest potential
To operate a full-scale entanglement-based quantum network at its fullest potential requires robust management and orchestration servicing multiple nodes, connections, and applications simultaneously. Optimized management and orchestration of network resources can ensure that multiple users and multiple applications are capable of running at the same time on the network in an equitable manner. Additionally, there exists a rate / fidelity tradeoff: some applications may require very high-quality entanglement, whereas other applications may require higher rates of entanglement at lower fidelities. Navigating this trade off to meet those quality requests for different users and different applications will have to be done with robust network management and orchestration software.
Supporting multiple topologies enables quantum networks to dynamically route and use the resources in the network for different connections and applications. Being agile in the implementation of entanglement-based quantum networks, as well as in the operation of them, is critical to utilizing these networks to full potential. Being agile includes being able to test new protocols and applications, being able to integrate new pieces of hardware and software as the technology matures, and potentially connecting to other entanglement-based quantum networks and other quantum ecosystems that may be geographically nearby. This allows the network stakeholders to leverage a variety of quantum resources, grow ecosystems, build relationships and connect with other businesses building this technology out globally, and enable a bigger footprint for a network’s capabilities.
Expansion of entanglement-based quantum networks will enable the global Quantum Internet. The Quantum Internet is a network of entanglement-based quantum networks, where many different pieces of quantum technology are integrated together (e.g. quantum computers, quantum sensors) and can all coexist on a global network. The Quantum Internet will bring a technological revolution. We can’t even imagine all the possibilities yet but just as the classical Internet has changed the world, the Quantum Internet will change it too.
Real world entanglement-based quantum network deployments
Entanglement-based secure networking efforts are ongoing in the US and Canada, and below you can see a map of some notable deployments and planned deployments.
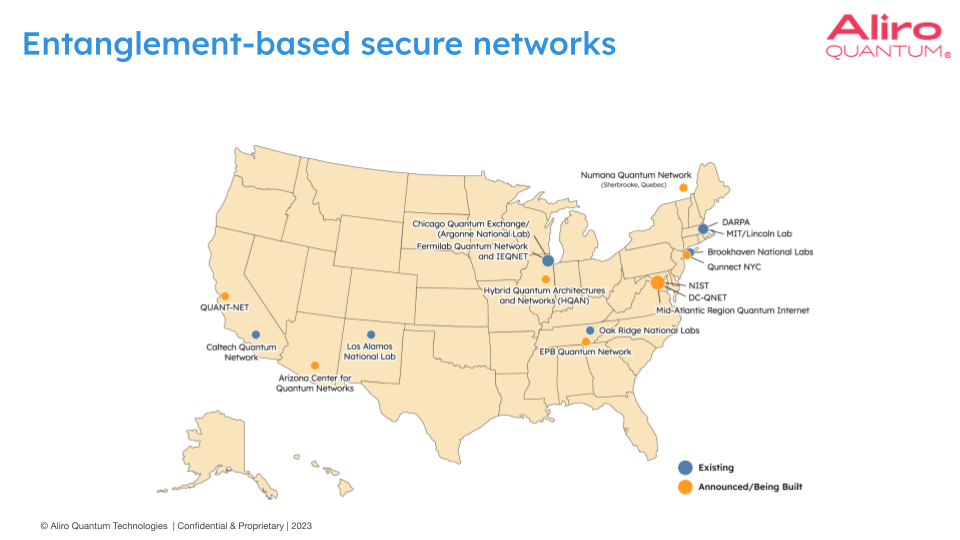
Of course, this is not a comprehensive mapping of all the entanglement-based secure networks being built today. In blue, above, you can see some existing quantum network test beds that have been stood up. In orange, you can see some of the announced networks that are currently building being built.
Deploying a full-scale entanglement-based quantum network is an exciting phase of network implementation, where the true power of entanglement-based technology is unlocked. This is also a journey. Whereas the first two stages of quantum network deployment (stage one: Design and Emulation, and stage two: Pilot and Trial) have a clear endpoint, this third stage of full-scale deployment doesn't have a clear endpoint. As with classical networks, there will be maintenance and updates to upgrade performance of the entanglement-based quantum network. This stage requires a plan for growth, and it's never too early to start.
Being an early adopter of full-scale quantum networking is an opportunity for an organization as a first-mover advantage, as well as the opportunity to shape the field going forward and grab a hold of the entanglement-based quantum network market share. Building an entanglement-based-quantum-network-as-a-service venture can also be extremely valuable: internally to your organization, and also as an external offering to customers and end users. The value of building trust as a quantum-safe or quantum-forward organization cannot be overestimated: given the geopolitical contexts and the cybersecurity context that we live in today, building trust as a safe organization that's thinking about the latest best-practices in cybersecurity is a potentially impactful strategic move. Entanglement-based quantum networks will require organizations to invest in infrastructure, develop their workforce, and coordinate their systems and processes before realizing the full value of this emergent technology. By starting now, an organization will be well-positioned to employ the technology to competitive benefit.
