Report: Quantum Network Simulation for Cloud Providers
By simulating how quantum systems behave in real-world conditions, quantum network simulation aids engineers and technologists in modeling the trade-offs of different configurations.

By simulating how quantum systems behave in real-world conditions, quantum network simulation aids engineers and technologists in modeling the trade-offs of different configurations.
Click here for a downloadable pdf of this white paper.
Executive Summary
The Quantum Threat and the Quantum Solution
Efficient and Effective Quantum-safe Security for Cloud Workloads
A Phased Approach to Quantum-powered Security for the Cloud
Role of the Quantum Network Simulator
Aliro Simulator: Advancing Quantum Networking Through Comprehensive Simulation
Key Features and Capabilities
Simulation-Aided Design
Design Validation and Optimization
Benefits of Using Aliro Simulator
The high-volume and often sensitive nature of the data accessed in cloud platforms make cloud infrastructure a high-value target for advanced threats stemming from AI and quantum computing. Even before quantum computers render current encryption schemes obsolete, sensitive cloud-based data can be compromised by Harvest Now Decrypt Later (HNDL) attacks, where adversaries intercept encrypted data and store it until they have the resources to decrypt it. Safeguarding against these advanced threats requires proactive investment in quantum-secure architectures today.
Public key infrastructure is vulnerable to quantum attacks. The classical methods in place today, including Post-Quantum Cryptography (PQC), rely on the assumption that even quantum computers cannot solve certain specific hard mathematical problems fast enough to break the encryption. Quantum networking offers the most effective protection: provably secure communication enabled by the laws of quantum physics.
Deploying quantum networks requires careful evaluation of quantum hardware, protocols, and topologies. Quantum network simulation allows cloud providers to simulate and iterate quantum network designs before any hardware investment. Aliro Simulator provides a low-risk virtual environment for modeling the performance and utility of quantum networks under real-world conditions.
For enterprise cloud operators, quantum network simulation is a time - and cost-saving R&D tool that de-risks the deployment of quantum networks. By simulating how quantum systems behave in real-world conditions, Aliro Simulator validates performance of the network and aids engineers and technologists in modeling the trade-offs of different configurations.
Organizations that invest in the foundations of their quantum network today will be better positioned to adapt as quantum technologies become mainstream. Aliro Simulator gives cloud providers an early advantage by enabling them to design, test, and validate quantum networks that use the laws of physics to guarantee that even future quantum computers cannot decrypt sensitive data.
As quantum computing advances, public key infrastructure is increasingly vulnerable. Even before a cryptographically relevant quantum computer arrives, Harvest Now Decrypt Later (HNDL) attacks are already a serious threat. In HNDL attacks, adversaries intercept encrypted data now and store it, with the intention of decrypting it once quantum computers are capable.
This reality presents a high-stakes challenge for organizations that manage or rely on cloud infrastructure. Cloud networks frequently carry information that must remain secure for extended periods of time. Mitigating the risk to these links is a high priority. There are several protections available today that can protect sensitive data from HNDL attacks and the arrival of powerful quantum computers: Post-Quantum Cryptography (PQC), Quantum Key Distribution (QKD), and Quantum Secure Communication (QSC).
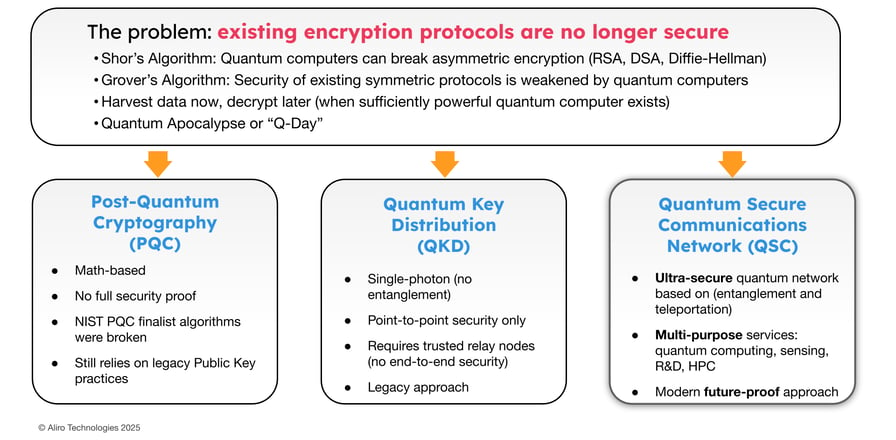
Post-Quantum Cryptography (PQC). PQC is a well known methodology today. PQC consists of math-based algorithms that replace the legacy math-based algorithms that are used in public key encryption. While not provably immune to future attacks, PQC significantly improves upon legacy algorithms such as RSA. The National Institute of Standards and Technology (NIST) has finalized a set of candidate standards following rigorous public testing. Several early contenders failed, with some unable to withstand basic decryption attacks using conventional laptops. In cloud environments, PQC is essential for securing key exchange, data integrity, and authentication across distributed services, APIs, and customer-facing applications. PQC is an essential first step for cloud security, but it may be vulnerable to future attacks we aren’t aware of today.
Quantum Key Distribution (QKD). QKD advances security by leveraging quantum physics to establish shared keys. Using single encoded photons, also known as qubits, QKD creates encryption keys that are more secure than those generated by classical methods. This is what is referred to as prepare-and-measure QKD: a point-to-point security mechanism that requires trusted relay points to extend the distance of the links. Some vulnerabilities are introduced by these trusted relay points due to data being exposed in the clear at each relay. While valuable for some links, QKD's end-to-end security limits make it less ideal for high-capacity, multi-node cloud links. For those links where QSC is not feasible but physics-based protections are desired, QKD can be a helpful method.
Quantum Secure Communications (QSC). QSC is an ultra-secure physics-based methodology that leverages entanglement and teleportation. This is the most secure implementation for protecting the high-volume links that carry the most sensitive data. QSC enables ultra-secure, scalable communication that does not require the physical transmission of encryption keys; the secure keys are generated and known only at the endpoints. QSC is well suited for cloud links with the most demanding confidentiality requirements, and also supports future applications such as scaling quantum processing power or distributed quantum sensors that could enable future capabilities hosted in the cloud.
The timeline to Q-Day, the day a cryptographically relevant quantum computer (CRQC) comes online, continues to accelerate. Since the advent of Shor’s algorithm in 1994, researchers and governments have acknowledged the need to replace vulnerable encryption systems. NIST began the formal process of standardizing post-quantum cryptography (PQC) in 2016. In 2019, Google achieved quantum supremacy. And more recently, research from China and new hybrid quantum-classical algorithms suggest that the number of qubits needed to break RSA-2048 could be significantly lower than previously estimated. While conservative estimates project a CRQC to be 10 years away, aggressive forecasts suggest it could arrive in as little as 3–5 years. Gartner recently estimated that a CRQC could arrive by 2029, and that asymmetric cryptography could be fully broken by 2034. For organizations that operate mission-critical data center infrastructure, waiting for this inevitability is a risk not worth taking. But what can be done now to prepare?
Critical cloud communications such as inter-region connectivity, hybrid connectivity, and cross-cloud / multi-cloud connectivity could be protected at the highest level of security using QSC; secure keys are never transmitted on the network, and tampering with these keys is immediately detectable. Simulators like the Aliro Simulator can model entanglement-based quantum networks, evaluate performance under varying conditions, and optimize integration with existing cloud infrastructure. By enabling experimentation without physical risk, Aliro Simulator provides helpful analysis on how to protect data beyond Q-Day. As the countdown to Q-Day accelerates, quantum network simulation lays the foundation for quantum-powered security.
Not every connection in the cloud is equally at risk when it comes to sophisticated quantum attacks. Traffic volume, data sensitivity, and exposure to untrusted networks can help cloud providers determine the most efficient and effective quantum-safe technique to deploy. A tiered, risk-based model starts with Post-Quantum Cryptography (PQC) at the edge and scales up to Quantum Secure Communications (QSC) at the most critical cloud interconnects.
PQC should be used everywhere that already runs TLS/SSH/IPsec: Browsers and mobile apps terminating at provider points-of-presence, CDN edges, API gateways. PQC offers a reasonable balance between protection and implementation effort for these mid-tier environments.
In medium-risk zones, a hybrid strategy is warranted. PQC remains the baseline, but organizations should augment it with QKD where feasible, and begin integrating QSC wherever possible. QKD can be used for East-West traffic among micro-services, service-mesh mTLS, container orchestration, and connecting big aggregation points (region gateways, large campuses).
In high-risk zones, plan for QSC where regulations or business sensitivity justify the premium. Private, co-located, and hybrid cloud environments are all areas of the network that carry massive volumes of high-value, highly sensitive data. This is where the risk of quantum-enabled breaches is greatest, and where the strongest defenses are necessary. QSC should be the main security methodology for these areas.
For cloud operators, integrating quantum networks into existing infrastructure can appear daunting due to complexity, cost, and challenges in implementation. Designing quantum networks requires precision in modeling component behavior, noise and environmental factors, protocol and device compatibility, and performance scalability. A phased, strategic approach makes adoption of quantum-powered security both practical and scalable. The first step in a phased approach is simulation.
Quantum network simulators such as Aliro Simulator play a critical role in the planning phase. By modeling entanglement-based network topologies, testing protocol configurations, and assessing performance under realistic network conditions, a simulator helps organizations design, validate, and optimize quantum network behavior for their unique situation. Incremental expansion of the quantum network can then add more interconnects, cloud gateways, or geographically distributed resources. This simulation-led approach reduces risk, aligns with capital planning cycles, and helps organizations build internal quantum expertise over time.
Quantum network simulation is the foundation for planning and validating the integration of quantum networking with data center-to-data center (DC-to-DC), data center-to-headquarters (DC-to-HQ), and headquarters-to-cloud (HQ-to-Cloud) architectures. Simulation enables:
Topology planning. Modeling the existing fiber infrastructure and characteristics your quantum network will run on.
Hardware modeling. Evaluating entangled photon source placement, quantum memories, and photonic interfaces at different levels of abstraction: from individual device behavior up to a wide area network.
Performance optimization. Assessing latency, fidelity, key generation rates, and fault tolerance.
Integration strategies. Testing how quantum systems interoperate with existing classical encryptors, routers, and DWDM systems as well as interoperability between quantum network devices.
Aliro Simulator supports modeling from the smallest photonic component to full-scale multi-site quantum-secure networks.
Entanglement-based quantum networking holds immense potential for secure communication, enhanced cloud access, and networked quantum computers. However, developing and deploying quantum networks presents significant challenges, demanding meticulous design, validation, and implementation. Aliro addresses these challenges with its robust Aliro Simulator, a scalable cloud platform and simulation pipeline designed to facilitate the development and optimization of quantum networks. This white paper provides an overview of the Aliro Simulator, highlighting its features, capabilities, and benefits for researchers and developers in the quantum networking space.
Aliro Simulator offers a comprehensive suite of tools and functionalities to support the simulation and analysis of quantum networks. Key features include:
The Aliro Simulator plays a critical role in simulation-aided design, particularly for Entanglement Purification and Photon Sources (EPPS). By providing a virtual environment for testing and refining EPPS designs, the simulator enables developers to optimize performance and identify potential issues before physical implementation.
Design Validation and Optimization
Theoretical formulas for quantum network behavior can quickly become intractable, making simulation essential for design validation.
The Aliro Simulator facilitates:
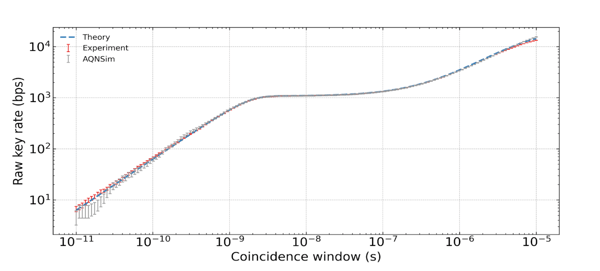
Figure 1. Comparison of Theoretical, Experimental and Aliro Simulation Results for Key Rate
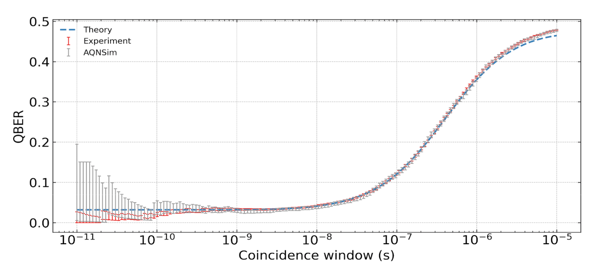
Figure 2. Comparison of Theoretical, Experimental and Aliro Simulation Results for Qubit Error Rate
Aliro Simulator is a powerful tool for advancing quantum networking research and development. Its comprehensive features, scalable platform, and robust simulation capabilities empower researchers and developers to design, validate, and optimize quantum networks effectively. Aliro simulation results provide a tight correlation with both theoretical and hardware-based experimental results. By leveraging the Aliro Simulator, organizations can accelerate their journey towards realizing the full potential of quantum networking and its transformative applications.