-3.png?length=1200&name=Aliro%20Blog%20gfx%20(1920%20x%20977%20px)-3.png)
What is EaaS?
Entanglement-as-a-Service (EaaS) is the fundamental service provided by quantum networks. Using EaaS, quantum networks can provide a range of applications, from secure communication to distributed quantum computing.
Rather than support a specific application, EaaS networks provide entanglement that can be used by a variety of applications. When two endpoints are connected to an EaaS network, they can teleport arbitrary quantum states between qubit memories. This enables, for example, clustered quantum computing because it allows different quantum computers to share quantum state and perform distributed quantum computations.
This contrasts with another kind of quantum network you may have heard of—Quantum Key Distribution (QKD) networks.
QKD networks differ from EaaS networks in that they are special-purpose. Where EaaS networks distribute entanglement, QKD networks use an approach called prepare-and-measure. Prepare-and-measure networks operate in three steps: (1) A sending endpoint prepares one of a handful of predetermined states on a single local qubit; (2) the qubit is immediately sent to another endpoint; and (3) the qubit is immediately measured at the receiving endpoint. These networks have no quantum memory, so when an endpoint receives a qubit, it must immediately measure it, collapsing the wave function and destroying the state.
Prepare-and-measure works for QKD on short distances, but we need quantum entanglement for other use cases such as clustered quantum computing and long-distance secure communication.
The following diagram shows an example of an EaaS quantum network:
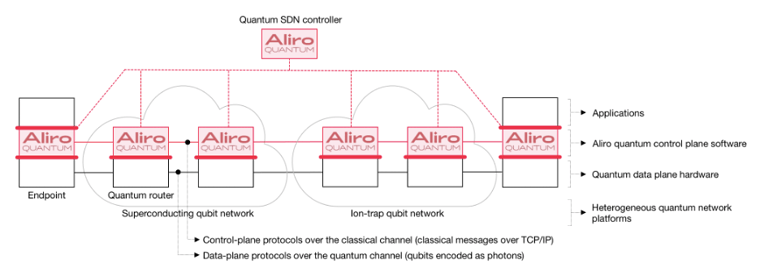
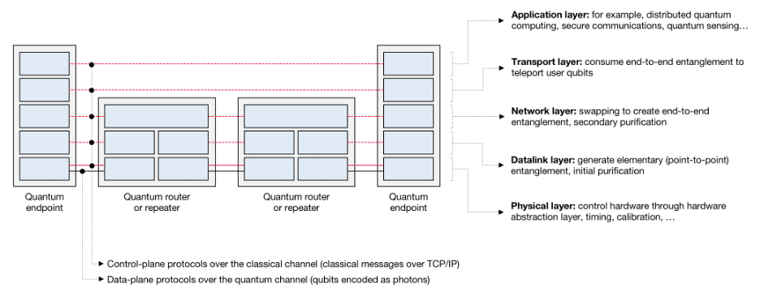
As shown in the next figure below, the quantum routers / repeaters and the endpoints in the EaaS quantum network run various protocols to:
- Generate end-to-end entangled qubits (using elementary entanglement generation, purification, and swapping).
- Deliver the end-to-end entangled qubits to the endpoints at the desired rate (Bell pairs per second) and at the required quality (fidelity).
- The endpoints use teleportation to teleport the user qubits (the actual data) across the network.
3 Ways that EaaS networks enable secure communications and more
How do EaaS networks go beyond existing QKD networks to provide quantum network security and other quantum network applications? Here are three key differences:
1. EaaS networks are inherently secure because they use teleportation
EaaS networks use quantum teleportation to communicate without ever sending secret user qubits across the fibers or the quantum routers in the network. Instead, the secret user qubits are teleported directly from the source endpoint to the destination endpoint. They never touch the fibers or quantum routers and hence they cannot be observed by an eavesdropper on the network.
By contrast, in a QKD network, the secret key bits themselves are transmitted through the optical fibers and relay nodes in the network. The secret key bits do touch the network and hence an eavesdropper can observe the secret key bits as they traverse the network. Also, the secret user data (though encrypted) travels across the network and can be intercepted by an eavesdropper.
Luckily, the laws of quantum physics dictate that the amount of noise increases when an eavesdropper is present: observing a quantum state causes the quantum state to change. The QKD protocol relies on classical post-processing algorithms and sophisticated statistical analysis of the observed amount of noise to detect the presence of an eavesdropper. If the presence of an eavesdropper is detected, the key material is not used because it is deemed unsafe.
2. EaaS networks can provide long-distance secure communication
Existing commercially available QKD products only support point-to-point connections up to about 150 km distance (this is called the repeaterless bound). Actual practical distances for point-to-point connections are less, around 50 km, because the key production rate decreases exponentially with distance.
There are some experimental QKD technologies (for example MDI QKD and twin field QKD) that support star topologies and/or larger distances (up to 600 km in theory) but these technologies are not yet commercially available.
To extend beyond these short distances and limited topologies, QKD networks use trusted intermediate relay nodes. Relay stations are placed along a chain between nodes, where the secret key is measured and regenerated. This allows for a connection to extend much further, but requires revealing the secret key to the relay node. This makes QKD unsuitable for scenarios where the users rely on external networks.
The first commercially available EaaS networks will also be point-to-point networks and will also be subject to the same distance limitations of 50 to 150 km. Key applications at this range include clustered quantum computing and metropolitan-area secure networks.
Quantum repeaters offer the key to extending networks to longer distances. Once quantum repeaters and quantum routers become available, EaaS networks will be able to support quantum networks that have arbitrary topologies (not just point-to-point or star) and that can support large endpoint-to-endpoint distances. Quantum repeaters have been demonstrated in the lab. The enabling technologies for quantum repeaters (i.e. quantum memories) will become commercially available off-the-shelf just as single photon sources and detectors are today.
EaaS can support large distances and arbitrary topologies without relying on trusted nodes. Instead, EaaS networks use quantum repeaters or quantum routers. The main difference between a quantum repeater / router and a trusted node is that the secret key (or in fact any kind of user quantum data) is never exposed at any point in the network, either on the fibers or inside the quantum repeaters / routers. This means that the network user does not need to trust a network provider.
3. EaaS networks are general purpose instead of single purpose
The goal of EaaS networks is to deliver a resource—quantum entanglement—which can then be used by applications. In this way, EaaS networks are fundamentally different from special-purpose networks, like QKD networks. QKD networks are built to support a specific application, namely key distribution for secure communication. In EaaS networks, entanglement can then be consumed by the applications, such as:
- Secure communications
- Clustered quantum computing
- Distributed quantum computing
- Blind quantum computing
- Quantum time synchronization
- Quantum sensing
- Other current and future use cases
As a classical analogy, the plain old telephone service (POTS) network at the end of the 20th century was a special-purpose network that only provided voice service. It has now been replaced by voice-over-IP (VOIP) which is just one of many services running over the general-purpose Internet.
How to make the quantum leap
Service providers and enterprises interested in protecting their data using EaaS have several options to begin building in-house expertise. Providers can begin by working with a quantum networking provider to understand how they can add EaaS functionality to their network. As a first step, providers can use quantum network simulators to build knowledge without investing in a physical network. If you are interested in learning more about how EaaS can work with your network, please get in touch.
